提示:本文仅供参考,禁止用于非法活动
文章目录
前言 一、页面分析 二、数据获取 三、总结前言
目标网站:aHR0cHM6Ly9iei56enptaC5jbi9pbmRleA==
一、页面分析
进到首页后,翻页一下,就可以看到目标接口,翻页的时候会出现滑块,抓包看下参数,会有个debugger,直接右键跳过即可,然后某些网页如果特别卡的话,都是一些定时器在作怪,直接输入下面这一行搞顶
for (var i = 1; i < 99999; i++) window.clearInterval(i);
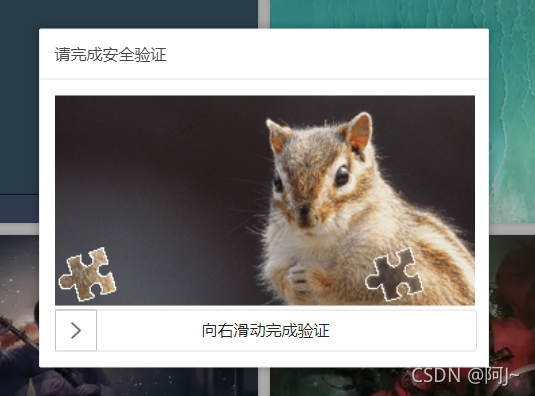
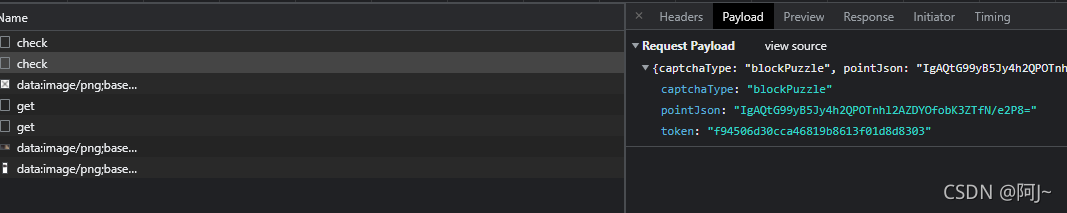
时曾相识的参数,翻了翻之前的文章,我记得我是写过的,竟然没找着
后来才记起是写在了公众号上:python爬虫和阿J的逆向
所有的步骤基本是一样的,就是最后用到校验后的数据captcha,是不需要再经过base64编码的
二、数据获取
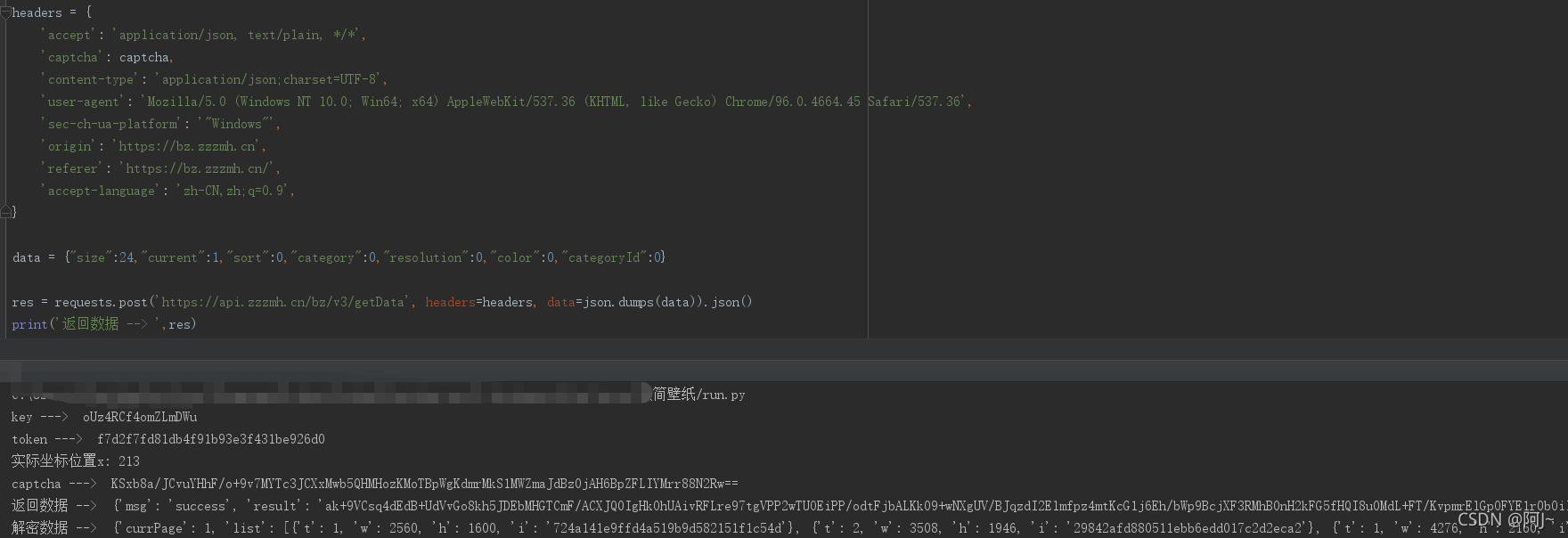
可以看到返回数据也是做了加密的处理嗷,直接跟栈找解密位置吧
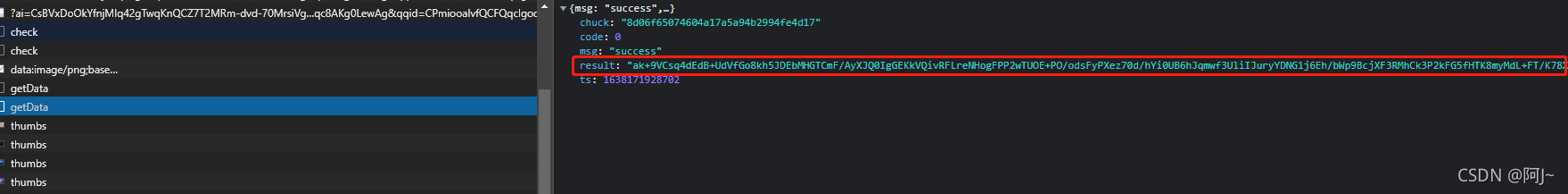
就一直网上根根就找到了解密的位置
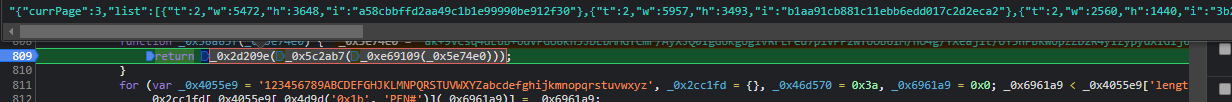
掉了三个函数,看不懂啥类型的解密,直接扣他完事
function _0x2d209e(_0x5e74e0) {
for (var _0x536c72, _0x3545f0, _0x26b638 = '', _0x3d15b0 = 0x0; _0x3d15b0 < _0x5e74e0['length'];)
_0x536c72 = _0x5e74e0[_0x3d15b0],
_0x3545f0 = 0x0,
_0x536c72 >>> 0x7 === 0x0 ? (_0x26b638 += String['fromCharCode'](_0x5e74e0[_0x3d15b0]),
_0x3d15b0 += 0x1) : 0xfc === (0xfc & _0x536c72) ? (_0x3545f0 = (0x3 & _0x5e74e0[_0x3d15b0]) << 0x1e,
_0x3545f0 |= (0x3f & _0x5e74e0[_0x3d15b0 + 0x1]) << 0x18,
_0x3545f0 |= (0x3f & _0x5e74e0[_0x3d15b0 + 0x2]) << 0x12,
_0x3545f0 |= (0x3f & _0x5e74e0[_0x3d15b0 + 0x3]) << 0xc,
_0x3545f0 |= (0x3f & _0x5e74e0[_0x3d15b0 + 0x4]) << 0x6,
_0x3545f0 |= 0x3f & _0x5e74e0[_0x3d15b0 + 0x5],
_0x26b638 += String['fromCharCode'](_0x3545f0),
_0x3d15b0 += 0x6) : 0xf8 === (0xf8 & _0x536c72) ? (_0x3545f0 = (0x7 & _0x5e74e0[_0x3d15b0]) << 0x18,
_0x3545f0 |= (0x3f & _0x5e74e0[_0x3d15b0 + 0x1]) << 0x12,
_0x3545f0 |= (0x3f & _0x5e74e0[_0x3d15b0 + 0x2]) << 0xc,
_0x3545f0 |= (0x3f & _0x5e74e0[_0x3d15b0 + 0x3]) << 0x6,
_0x3545f0 |= 0x3f & _0x5e74e0[_0x3d15b0 + 0x4],
_0x26b638 += String['fromCharCode'](_0x3545f0),
_0x3d15b0 += 0x5) : 0xf0 === (0xf0 & _0x536c72) ? (_0x3545f0 = (0xf & _0x5e74e0[_0x3d15b0]) << 0x12,
_0x3545f0 |= (0x3f & _0x5e74e0[_0x3d15b0 + 0x1]) << 0xc,
_0x3545f0 |= (0x3f & _0x5e74e0[_0x3d15b0 + 0x2]) << 0x6,
_0x3545f0 |= 0x3f & _0x5e74e0[_0x3d15b0 + 0x3],
_0x26b638 += String['fromCharCode'](_0x3545f0),
_0x3d15b0 += 0x4) : 0xe0 === (0xe0 & _0x536c72) ? (_0x3545f0 = (0x1f & _0x5e74e0[_0x3d15b0]) << 0xc,
_0x3545f0 |= (0x3f & _0x5e74e0[_0x3d15b0 + 0x1]) << 0x6,
_0x3545f0 |= 0x3f & _0x5e74e0[_0x3d15b0 + 0x2],
_0x26b638 += String['fromCharCode'](_0x3545f0),
_0x3d15b0 += 0x3) : 0xc0 === (0xc0 & _0x536c72) ? (_0x3545f0 = (0x3f & _0x5e74e0[_0x3d15b0]) << 0x6,
_0x3545f0 |= 0x3f & _0x5e74e0[_0x3d15b0 + 0x1],
_0x26b638 += String['fromCharCode'](_0x3545f0),
_0x3d15b0 += 0x2) : (_0x26b638 += String['fromCharCode'](_0x5e74e0[_0x3d15b0]),
_0x3d15b0 += 0x1);
return _0x26b638;
}
function _0x5c2ab7(_0x5e74e0) {
for (var _0x536c72 = [-0x6f, 0x34, 0x5b, 0x41, -0x41, 0x74, 0x77, 0x6a, -0x79, -0x52, -0x5, 0x50, 0x33, 0x61, 0x44, -0x53, -0x70, -0x33, 0x17, -0x2e, -0x22, -0x72, -0x37, -0xb, -0x7f, 0x5a, 0x21, 0x16, -0x1f, 0x32, -0x11, 0x14, -0x2c, 0xf, -0x5e, -0x7b, 0x76, -0x17, -0x3d, 0x72, 0x47, -0x68, -0x7e, -0x75, -0x51, -0x36, -0x12, -0x6e, -0x4, -0x5f, -0x5b, 0x5e, -0x50, -0xe, 0x78, 0x69, 0x55, 0x68, -0x56, -0x6c, 0x43, 0x19, 0x65, 0x6c, 0x10, -0x69, 0x6f, -0xa, 0x75, -0x49, 0x4d, 0x59, -0x1d, -0x62, -0x44, 0x70, 0x6b, -0x1, 0x56, 0x79, 0x58, -0x65, -0x7c, 0x45, -0x1e, -0x8, -0x71, -0x4a, -0x76, 0x39, -0x19, 0xc, -0x73, -0x6a, 0x5f, 0x7f, 0x54, 0x7c, -0x66, -0x1c, 0x49, 0x2b, -0x3c, 0x1c, 0x2e, 0x73, 0x1e, 0x7a, -0x4b, 0x7d, -0x43, -0x4d, 0x3, -0x7, -0x35, -0xd, 0x35, 0x4e, -0x48, 0x1, 0xb, -0x47, -0x27, -0x4f, -0x3, 0x13, 0x29, 0x7e, -0x2b, -0x7d, -0x1b, 0x22, 0x3f, 0x8, 0x48, -0x23, -0x29, -0x3f, 0x3c, -0x18, 0x66, 0x2f, -0x77, -0x67, -0x16, 0x2d, 0x3b, 0x40, -0x60, 0x31, 0x53, -0x6b, -0x78, -0x39, -0x46, 0x0, -0x26, -0x54, -0x28, 0x18, 0xe, 0x30, 0x1d, 0x2c, -0x24, -0x2f, 0x38, -0x5c, 0x26, 0x25, 0x4, -0x32, 0x67, 0xa, -0x59, 0x37, 0x71, -0x1a, 0x6e, 0x36, 0x24, -0x14, -0x4e, -0xc, -0x74, 0x46, -0x25, 0x5, -0x3e, -0x4c, -0x30, -0x40, 0x4f, 0x64, 0x28, 0x6, -0x3a, -0x5a, -0x13, -0x9, 0x27, 0x5d, -0x63, 0x15, 0x7, 0x1a, -0x2, 0x1b, -0x2d, 0x51, 0x3a, -0x7a, 0x4c, -0x42, 0x2, 0x5c, -0x2a, 0x62, -0x10, 0x9, 0x3d, 0x3e, -0xf, 0x63, -0x15, 0x1f, -0x38, 0x57, 0x11, -0x34, -0x45, -0x21, -0x3b, -0x55, 0x42, 0x4a, 0x12, -0x5d, -0x80, -0x57, -0x20, 0x2a, 0x20, -0x58, 0x6d, 0x60, 0xd, -0x6, 0x4b, -0x64, -0x31, 0x23, -0x61, 0x52, -0x6d, 0x7b], _0x3545f0 = 0x0, _0x26b638 = 0x0, _0x3d15b0 = 0x0, _0x5c2ab7 = new Array(), _0x9bd313 = 0x0; _0x9bd313 < _0x5e74e0['length']; _0x9bd313++) {
_0x3545f0 = _0x3545f0 + 0x1 & 0xff,
_0x26b638 = (0xff & _0x536c72[_0x3545f0]) + _0x26b638 & 0xff;
var _0x1ce2d3 = _0x536c72[_0x3545f0];
_0x536c72[_0x3545f0] = _0x536c72[_0x26b638],
_0x536c72[_0x26b638] = _0x1ce2d3,
_0x3d15b0 = (0xff & _0x536c72[_0x3545f0]) + (0xff & _0x536c72[_0x26b638]) & 0xff,
_0x5c2ab7['push'](_0x5e74e0[_0x9bd313] ^ _0x536c72[_0x3d15b0]);
}
return _0x5c2ab7;
}
function _0xe69109(_0x5e74e0) {
for (var _0x536c72 = atob(_0x5e74e0), _0x3545f0 = new Int8Array(_0x536c72['length']), _0x26b638 = 0x0; _0x26b638 < _0x536c72['length']; _0x26b638++)
_0x3545f0[_0x26b638] = _0x536c72['charCodeAt'](_0x26b638);
return _0x3545f0;
}
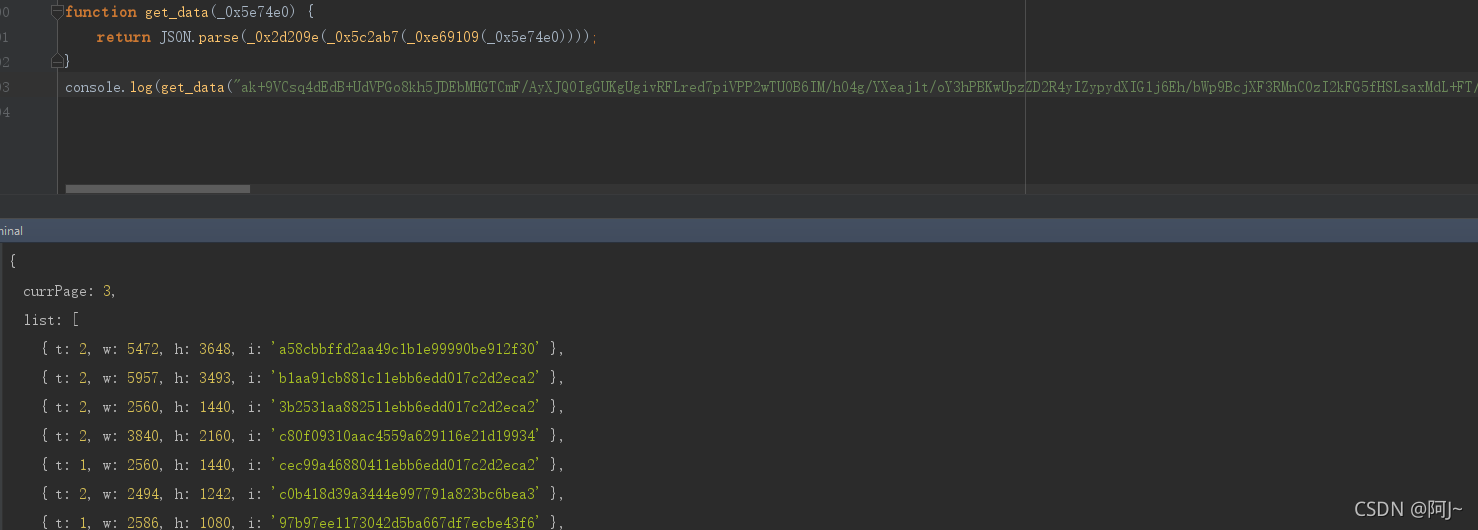
function get_data(_0x5e74e0) {
return JSON.parse(_0x2d209e(_0x5c2ab7(_0xe69109(_0x5e74e0))));
}
console.log(get_data("ak+9VCsq4dEdB+UdVPGo8kh5JDEbMHGTCmF/AyXJQ0IgGUKgUgivRFLred7piVPP2wTUOB6IM/hO4g/YXeaj1t/oY3hPBKwUpzZD2R4yIZypydXIG1j6Eh/bWp9BcjXF3RMnC0zI2kFG5fHSLsaxMdL+FT/K7pHyR1r5PVAE1rxNOiIiyTWi/+R3YxD5AnkRS+l/gAV6hZgJ0vuBLeHPQ4WPcc6kZGk5dO4FmTeSrRie+iq1IXGpFRaUvGgLxPwDqDP8BwHRgZR+ibYi3qQH4yLIKCFj7UDw9WxFzatw98cEpoLETl194ZxgiCrYehMENSU+TghsmJg1euPxe/DKNebCQnr1PGV4URmvOLLqTdSpHqwQcAuDUOh2OH1qt+67POe7OpsJiMRlb9fMyhagnw+2u3RHfC44UZBcVk3CuvUFx5kRSklErG8s11HJSLSJ4pUIamJKQyKVWXmrYwalKsFPvIL3QJxHbLYNGYZIE1G4lGDBHFGbB8MVCbCoRpln8k7Y0HAiYkjBTGAE0TIRVACtfE7Q3hjICbXb8eEBJWVwpKAYL7z/7ofMh6IeCXWBtJdk1aA1pEMT6uJ9qfhwBCW49L4+NPKgrdCrZLkSGggbpTaD70UbfDFF9dtuqy4sTzzrsUWLoId+TkRalXPIfb9tniwuI0RTTQxd6tJ8MTsiJ9Vw+VTrszseDrMb+vYt8apP+cGfKq2OkiotW5h2NKRn7LTd2gwPzqeKGnJq1UbGFjpsqqPjEtbiqc8HQxqlge3g3X6h1pgamOkgORLLisUj/SI5ckjT2SB4bnK7n7bUL6WRFc4mqN9VuN0gcTQkXJa95maG/rxGhBlFNjfh8O6UkNXQ6jlPb2y5d/EBURx4z74AjG2jnJtRj571fNoR6CVBgxgSobos/9+kNbkHRDEeoNB+M6aNmIx+QhVQePqLCahg7cz2a5xkCkUmONJmVYudQ5mxigQK7ijLKlje/W2oHtglEZWvKTnZ9l4udalcMgJ5GfEhnmZhjgD++8cGIXc10RSIeYDCVtySz/6x0GHhCiD6H1RQLRqOlpNtg2rjT66xnZBWmrZiOeC3UJF6Tg+8RpohALfW6Ym6kgJCDrcjMdJ/HyqBeDrE6pFoM0OYxb+1HXMEqqER3zQH4RX62/ASkqTzJ8HDHuvYW6ZThRi7NYQCWUN7ryiqnPOpPE2m4r5TFamw5VwKKDefh/bcKVdEy1VE19OY6g4YNNwXhlCyiKx5WnFFomIbi2UG42mRRvr8Z5kL6QkIh3xdRrVMYfPBZzbPTJmX6aeey3o5ZR+wVqkWIdEajn+i1jX0ymNIZIb+VnpVejD5SVM9+gP9swbv7xy4GJepJh6jwetMhxVybLkkTTUbeFpKdxnUfR2FoaRqMrklFM1pvjik3n5FTIO5TV6if/cgUIHyBmCjH4gTBn0tpxxGlpZ0Q2YKV0QJSHrvHa2ILGq1ZICcKQ5chh1lXQzAHqF5BcP79LlW2kxscaVtFzRKNZ6qWcVnZqxOBVzcaMEFUwVDMtR1DsxCQljGJyfkHSRFO9HFG4RPhSStLytOCdlN34I+vVsfELZEJ2+AupwPutvpLXV8i/2D0mhT+L8kVwlLbePFPoENjxH09v5TPbuLL1Kj64DuaFW55ayWoYQoT06QmgCsfBiBa0VdHCSP08MXyj6XbSLD7rlIPcgtlXuxF9oJPnk25U2WSnHkxW475Sjm2BWw+M1b9PGVZvTvqKp2whS9B7SWB5josyJxa1wXmL1pEQ8SUqjc1QdgRvtstGIKy73cJYQ30QMptmiauEmB74BZOo3G0T+3qd04JIHwsrh2t4E1/WV2Il5v0LKh9UohciYUmz1X+KMQen/QlfRQUM1Fi3f0h8LDPOk2KR/ZXeMDEGgeSuHqKEYN9Ofn1xM9uJdCGSizXo1FEomyvuBhqzfgzj8KE8mGrdfqm7KapQ6ea1P8s7tmEH68RUYVYRSvz58JN4yFYhCE/ALb7yK91WpCxxuOn6rsYoeGeOklbvz+Of4RGuP/BLshE4MRWhroAOV9KyUT1g8kCrHneCh073GPwrJo3uEMaXqvGbu9qgTXj+AAZwE="))
三、总结
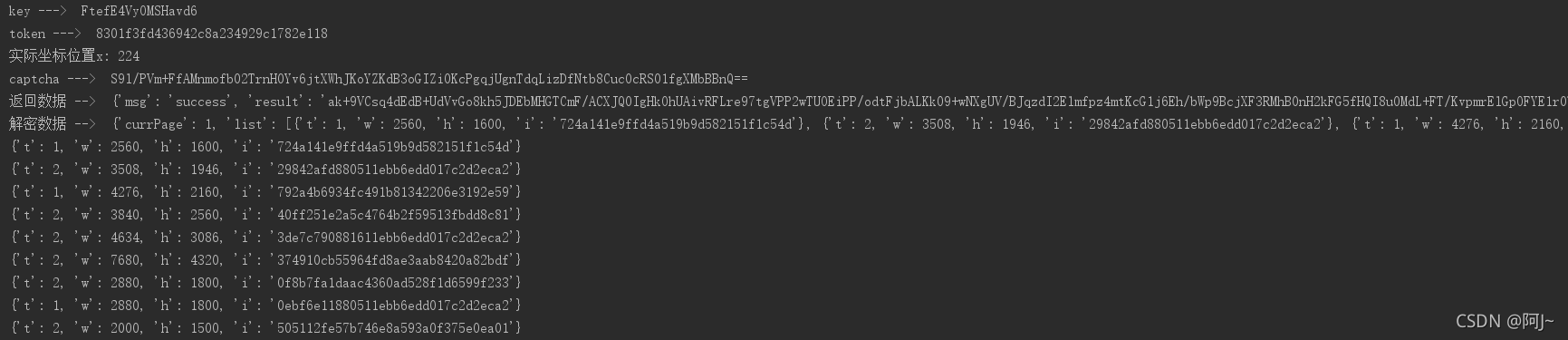
返回数据的i,就是图片的id了,拿着图片id去请求接口即可